
Ministry of Defence secrets exposed by people sending files to personal email accounts, documents show
Secret information belonging to the Ministry of Defence was exposed to hostile states when it was transferred from secure networks to personal email accounts, Sky News has learnt.
Although documents obtained by Sky News were redacted to obscure the nature of the secret information, they reveal a record number of security breaches in 2020 originating from the British military's private sector partners.
The rising number of security incidents raises questions about the UK's resilience to foreign espionage ahead of the government unveiling its Integrated Review on Tuesday, which will set out the strategic direction of Britain's defence and security apparatus.
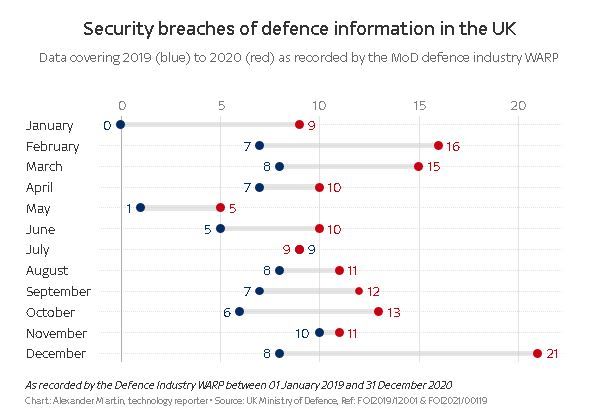
The redacted documents show that a total of 151 incidents were filed with the MoD's defence industry Warning, Advice and Reporting Point (WARP) in 2020, compared with just 75 in 2019.
"Every government contractor that processes MOD information is obliged to report security incidents to the Defence Industry WARP," explains a new page on gov.uk published last month.
Although the substance and outcome of these incidents is obscured, many of the records in the documents obtained by Sky News are followed by multiple paragraphs of redacted explanation, including numerous incidents when information was sent to personal email accounts."
Hostile states are known to target the personal email accounts of politicians and defence officials. Russian hackers allegedly stole secret trade deal papers from the personal email account of then cabinet minister Liam Fox ahead of the 2019 election.
The most extensive report, filed on 1 May 2020, runs several pages long and related to "data sent to unauthorised domain" - potentially indicating a phishing attack.
Two incidents in April were considered so sensitive that even the dates they occurred on were redacted.
Other incidents include potential compromises to MoD owned systems, a breach of a perimeter fence at an undisclosed location, infrastructure being misconfigured, and in one case missile containers being available for sale.
A spokesperson for the MoD said: "The MoD takes the security of its personnel, systems and establishments very seriously and continually seek to improve security incident reporting.
"We have recently introduced policy, processes and tools to make internal and external reporting easier and more efficient, and the increase in reports can be largely attributed to these improvements."
 The incidents raise questions about the UK's resilience to cyber spies.
The incidents raise questions about the UK's resilience to cyber spies.
Cyber attacks reported to the MoD and to the UK's National Cyber Security Centre, a part of GCHQ, are not referred to other regulators as a matter of course.
Businesses within the defence sector that lose personal data in a cyber attack are obliged to inform the data regulator, the Information Commissioner's Office, but this is not the case if non-personal state secrets are compromised.
Publicly listed companies are expected to inform the Financial Conduct Authority about any material incidents, including cyber attacks, whether personal data is lost or not.
The government's long-awaited Integrated Review - billed as the most significant strategic overhaul of the UK's foreign, defence, security and aid policy since the Cold War - is due to be launched on Tuesday.
In a sign of the likely political clashes ahead, the Conservative chair of the Defence Select Committee, Tobias Ellwood, warned ministers not to overlook the need to bolster existing military capabilities, telling Sky News: "We drop our guard on the conventional side at our peril."










